Advanced Security Service Insertion in OpenStack Cloud
OpenStack security groups offer a first line of defense for securing east-west traffic -- that is, traffic between virtual machines. The OpenStack Firewall-as-a-Service (FWaaS) plugin can help you configure firewall rules and policies on firewalls or Intrusion Prevention Systems (IPS). Unfortunately, these simpler solutions come with some limitations: security groups operate at the instance level, and FWaaS works on virtual routers within a project. The way FWaaS is currently implemented in OpenStack, a single set of rules is applied to all virtual routers on all subnets, which limits their flexibility and capabilities, thereby preventing companies from the deployment of enterprise-critical production workloads.
To combat this lack of flexibility, you might also implement a network virtualization platform or SDN to provide L2-L4 stateful firewalling features, delivering segmentation within virtual networks. But again, such traditional security technologies are port-bound, which means they lack the ability to control access based on application identity, and they may thus be ineffective for blocking today’s modern attacks.
This week, Mirantis and Palo Alto Networks are announcing a partnership to validate and simplify deployment of Palo Alto’s VM-Series virtual firewall as a virtual network function (VNF) on Mirantis OpenStack. Although VNFs are sometimes associated with telcos and other communications service providers (CSPs), this is frequently a misunderstood limitation. In fact, this joint solution is ideally suited to securing east-west traffic between applications, which is typically the largest traffic burden in any web-scale cloud running distributed and elastically-scalable applications.
The solution is engineered to protect applications and data from advanced cyber attacks in many different ways, including:
- Ease of deployment and provisioning: PAN VM-series firewall instances are quickly deployed on OpenStack VMs from Glance.
- Seamless traffic steering to the VM-Series firewall: The SDN controller steers traffic to the VM-Series firewall without requiring manual configuration changes to virtual networking attributes.
- Next-generation security for virtualized applications and data: The joint solution offers visibility and control at a user, application and content level.
- Advanced threat protection: VM-Series advanced threat protection addresses the complete attack lifecycle, with protection against exploits, viruses, spyware, malware and known and unknown threats, such as advanced persistent threats (APT).
VM-Series firewall on Mirantis OpenStack
The joint solution uses Fuel as the main deployment and management tool, and comprises a cluster that includes Openstack Controllers, OpenStack Compute nodes running the Contrail SDN Controller software, an OpenStack Compute node running Palo Alto VM-series virtual firewall, and general OpenStack Compute nodes, one or more of which runs an instance hosting the Palo Alto VM-Series firewall application.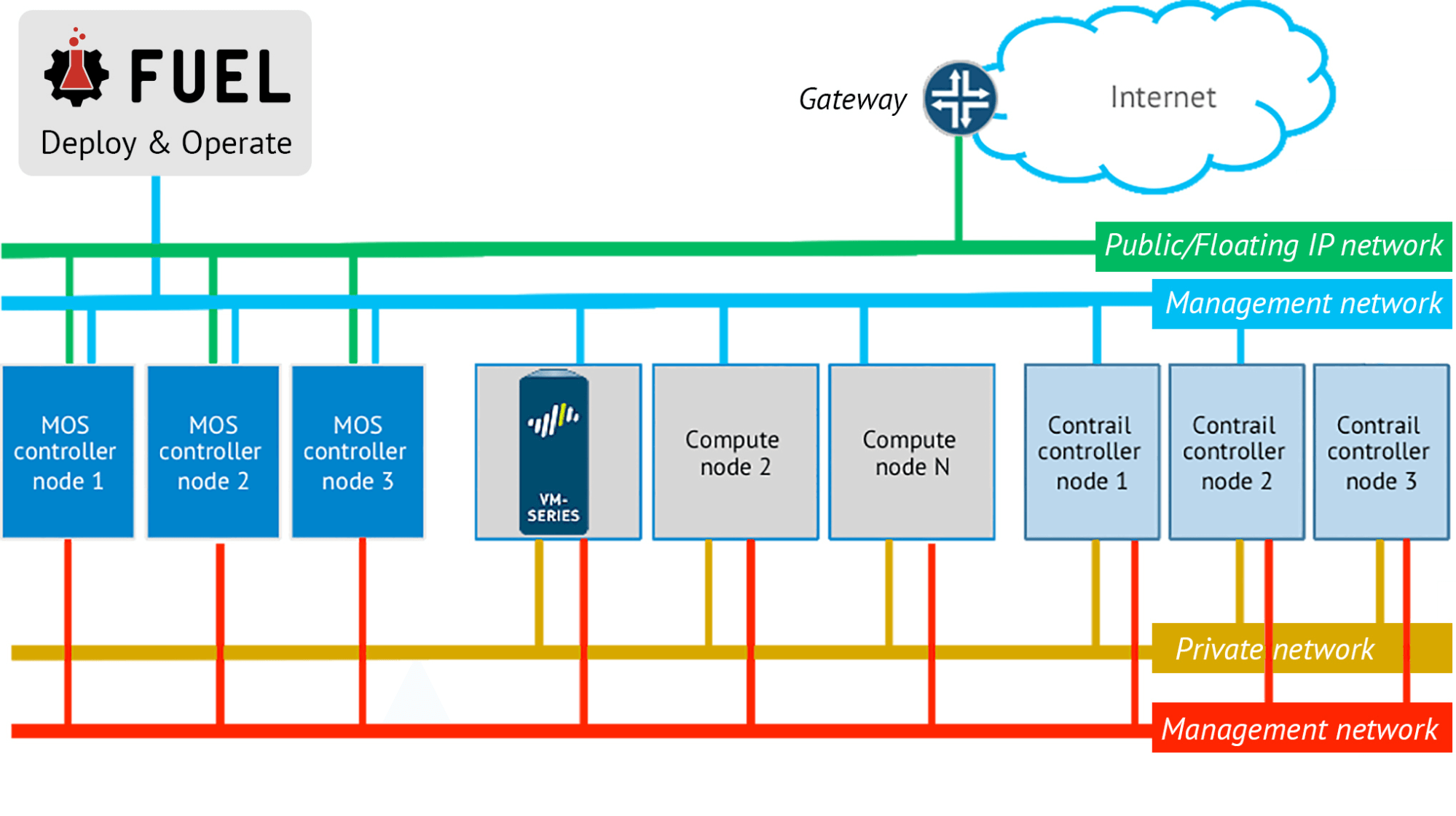
Figure 1 Mirantis OpenStack deployed with VM-Series Firewall
Advanced Security Service Insertion
One of the key components of this joint solution is the way it intelligently maps security policies to the VMs and seamlessly steers network traffic from designated workload VMs to advanced security appliances to enforce the proper policies.Traffic flows can be directed to, and processed by the Palo Alto VM-series firewall using one of three available service insertion (also called service chaining) modes supported by Contrail:
- In-network, where the virtualized firewall is between at least two networks, and packets are routed
- Transparent, where the virtualized firewall is transparent for communication between instances, and packets are switched
- Elastic Scale Out, which is similar as In-network, but a single service instance can use multiple virtual machines to scale out based on customer demand
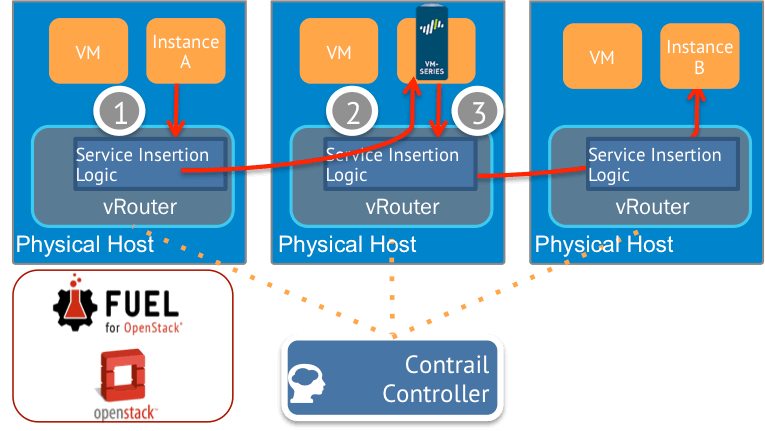
Figure 2 Traffic flow steering
For illustration of this joint solution, the service insertion traffic flow is shown in Figure 2 by using In-network mode as an example:- Traffic from Instance A is sent to the vRouter, where Service Insertion Logic that is managed by Contrail evaluates it.
- The Service Insertion Logic has been configured within Contrail by the user to create a Policy specifying that traffic from Instance A (panos-trust in Figure 3) destined for Instance B (panos-untrust in Figure 3) must go through the virtual firewall (panos-instance01 in Figure 3), so the traffic is forwarded to the VM-Series firewall (vFW on the diagram).
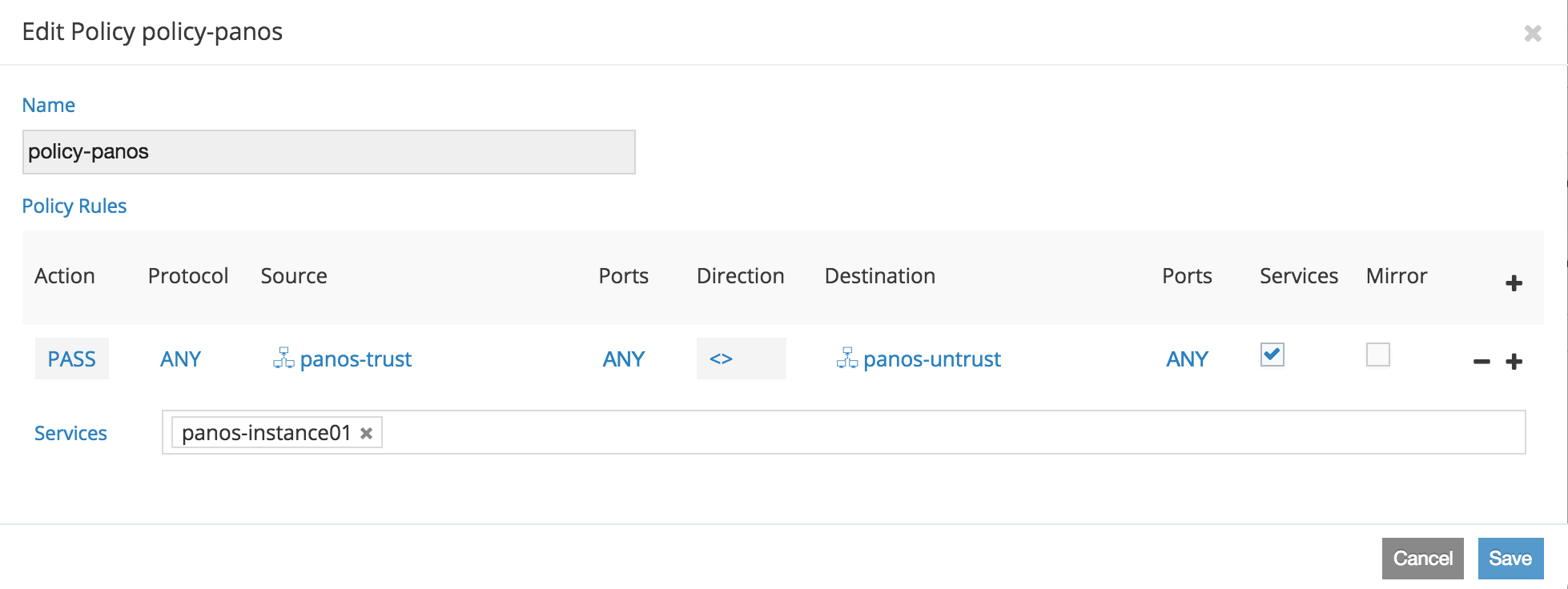
Figure 3: The policy in Horizon
- This is where the next-generation security is applied. The PAN VM-Series natively analyzes all traffic in a single pass to identify and control applications, limit access based on users, and prevent known and unknown threats. Mission-critical applications and data can be isolated in secure segments using Zero Trust (never trust, always verify) principles at each segmentation point.
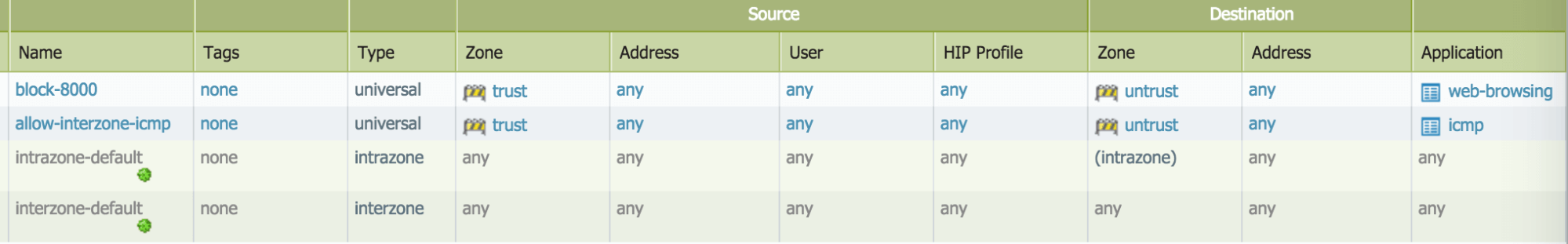
Figure 4: The ACL for the Palo Alto Networks VM-Series
The return traffic from the Host B goes through the similar steps to reach the Host A.Conclusion
Palo Alto Networks VM-series firewall application running on Mirantis OpenStack provides an integrated solution that enables IT organizations to unlock the benefits of OpenStack, from greater flexibility and agility to optimized capacity utilization and operational efficiencies, all without compromising security.If you're interested in getting more details about this solution, or if you want to check it out for yourself, we've published a runbook describing the reference architecture, installation and configuration steps for Mirantis Openstack, the Juniper Contrail plugin for Fuel, and Palo Alto Virtual Firewall when preparing an environment with service chaining.
This solution follows the launch of the Mirantis NFV Initiative, which included an NFV reference architecture to enable customers to easily deploy NFV solutions on OpenStack, and an OpenStack validation program for partner virtual network functions (VNFs). Moving forward, we will continue to bring VNFs, tools, infrastructure components, and complementary applications to the platform.






